What is Vulnerability Scanners Tools
Vulnerability Scanners Tools
Vulnerability scanning tools help identify system vulnerabilities by exposing weak areas of an organization’s IT ecosystem. These tools identify weaknesses in applications and systems and can help prevent cyber attacks. However, vulnerability scanning is not a substitute for proper firewall protection, which will keep unauthorized connections from entering the organization’s network.
Vulnerability scanning tools are available in different types, depending on the nature of the system they are meant to protect. Some tools provide non-intrusive scans, which identify system weaknesses without causing any interruption. Others use intrusive methods, which attempt to exploit vulnerabilities. While the former is more effective for detecting vulnerabilities, intrusive tools can cause significant problems in an organisation, disrupting systems, processes, and users.
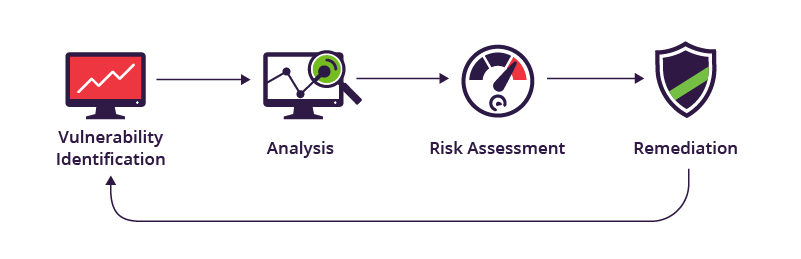
Vulnerability scanning tools can be used to find weaknesses in systems, such as weak passwords. They use various techniques and tactics to analyze network traffic and match it to an existing database. Based on the results, they can assign a risk rating to the individual security flaw. Some vulnerability scanners can scan all network ports to detect password breaches, suspicious applications or services, or coding flaws.
vulnerability scanning tools can be classified into two main categories: network-based and host-based scanners. Network-based scanners can detect vulnerable systems on wireless or wired networks. In addition, they can identify unknown perimeter points or devices in the network. Host-based scanners probe networks for specific vulnerabilities. These scanners can also provide a deeper analysis of vulnerabilities and their severity, helping to prioritize the most critical vulnerabilities for remediation.
What is Vulnerability Scanners Tools
Vulnerability scanning tools come in various styles and price ranges. There are paid versions as well as open-source ones. You should decide on the type that best suits your needs and budget. For example, a free vulnerability scanner such as Nikto2 can scan web applications and web servers. It also alerts you when there are server configuration issues, and can scan multiple networks in a short amount of time.
While vulnerability scanning tools can identify system vulnerabilities, they cannot remedy all security weaknesses. Third-party applications can also leave network devices vulnerable to security gaps. Some of these third-party applications can be outdated and may not update with the latest software. These security holes can be exploited by threat actors.
Vulnerability scanning tools are used by security professionals to monitor the integrity of web applications and websites. They are available in both authenticated and unauthenticated versions. The unauthenticated versions of vulnerability scanner software allow the tester to access the system without logging in. The vulnerability scanner software can then analyze this information to determine the weakness of the system.
Vulnerability scanning tools are important to ensure the security of an organization’s network. They can help identify vulnerabilities in a variety of systems, including databases, web servers, and operating systems. They can also scan containers and virtual machines.